It can be, but here's how to do it safely
We’ve gone from the philosophical concept of everything being connected to the physical reality that almost everything is connected. But there are those times where you can’t be connected to your home or work network, or a public WiFi hotspot. That’s where mobile hotspot tethering comes into play.

What is Mobile Hotspot Tethering?
Most phones or devices that can connect to the cellular network to access the Internet can share that connection. It can share it with devices in a very small area via WiFi or Bluetooth connection.
The part where you connect your device to a phone is the tethering part. Technically, anytime you connect two devices, wirelessly or with a wire like a USB cable, you’re tethering them.

The part where you set up the device connecting to the cellular network and share that connection is the mobile hotspot part. There will be a setting somewhere on your device that you can tell it to share its Internet connection. It’ll allow you to name the connection and set a password that you can give to other people so they can connect their devices.
How Can That be Dangerous?
There are a few ways that can cause a problem for you.
Your Cellular Data Bill Could Shoot Up Drastically
Did you ever share your WiFi password with a friend, only to find by the end of the night your Internet speed has slowed down to a crawl? Then you get on your router and you see half the apartment building is on your network? Sorry, but that’s human nature.

You give the password to one person. You ask them not to give it to anyone else. Then they’re talking with a friend of theirs and think, “Well, it’s only one more person. It won’t be a big deal. They won’t give the password to anyone else.” And that chain just continues.
Imagine that happening to your cell phone. Imagine that you’ve only got 5 GB of data, but 5 people are streaming Netflix. An hour later and you’re paying hundreds of dollars for someone to watch The Hills Have Eyes 3.

Your Information Could be Intercepted
Anytime you start sending information through the air, it becomes more vulnerable than if it’s travelling through the air. There are several ways that this could be done, such as a man-in-the-middle attack or intercepting the transmission via packet sniffing.
When someone tethers to your phone, you are creating a two-way street. If you’re the one providing access, you may be open to attack from your guest. If you’re the guest, you may be providing a way for the host to frolic through your phone.

Confidential Data Could be Leaked
If you’re a business owner, it might mean you losing data from your office. Picture this: a worker wants to access unauthorized sites at work, so they connect their laptop to their cellphone to circumvent your network. What’s to stop them from sending your client list or pricing strategy to someone else? You wouldn’t know and you couldn’t stop it.
Your Phone Battery Will Drain Much Quicker
Ok, so this isn’t dangerous, but if you are reliant on your phone for contacting family and friends this could be a problem. Your phone already uses a fair amount of power just to check and see if there’s a cell tower nearby, every now and again.
Then you make your phone into WiFi router and it takes more power to serve out access to whatever is tethered to it and is constantly talking to the cell tower. Where your phone battery might last a few days on standby, don’t expect it to last more than a few hours when you tether to it.

Something you will also notice is when your battery drains fast, it gets unusually hot. Like, too hot to put in your pocket. So that could be dangerous, especially if you leave it on a soft surface like a couch or bed.
How to Tether to Your Mobile Device Safely
Let’s do away with the notion of complete safety. That’s an illusion. The best you can hope for in life is a reasonable degree of security. That is, you’re satisfied that the bad things are much less likely to happen than the good things.
- Only use tethering when necessary. If you’re good at separating need from want, you’ll probably find that it’s almost never necessary.
- Only allow people to tether that you trust implicitly. For most people, that’s a short list. I’m talking about people you would trust with your bank card and PIN. Which you should never do either.
- Limit the amount of time that you allow tethering. If you need to tether to submit a report to your boss, get on the tether, e-mail the report, then shut off tethering.
- If your phone supports it, limit access to allowed devices only.
- If you allow tethering for any longer than necessary, keep an eye on what devices are connected. If you don’t recognize them, or there’s too many, shut of your mobile hotspot immediately.
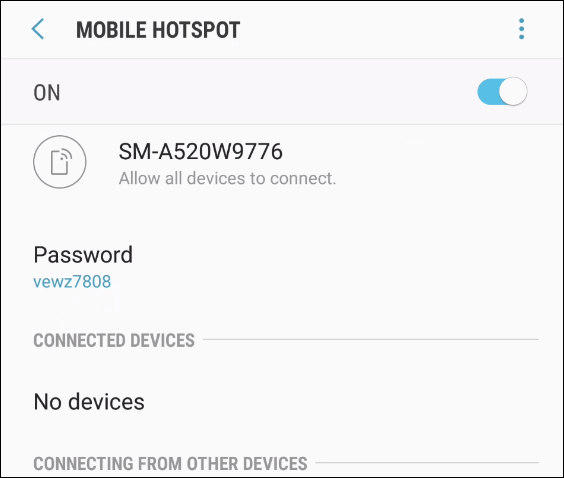
- Don’t use the same password for tethering more than once. If you’ve allowed a friend to tether once, and they see that your phone is hotspot again, they’re likely to jump on. Or, if the connection is saved, their phone might connect even without them knowing it. Now you’re downloading updates for their sports apps on your dime. Phones will often generate a password or PIN number for you. Some phones do this from a limited number of words or default PINs making it easier for someone to brute force a connection to your phone.
- Consider using a virtual private network when tethered to someone’s mobile hotspot. Really, you should use a VPN when connected to anyone else’s network, period.
- Make sure that you have somewhere to charge your phone. You’re going to drain it quickly and if it’s your only lifeline you must be able to charge it up quickly.
- If you’re a business owner and you don’t have Mobile Device Management (MDM) system and a strong computer and phone use policy in place, you’re going to pay sooner or later. Decide to pay a known amount for the MDM or decide to potentially lose your business by betting against the odds. Your call.
The Reality of Safe Mobile Hotspot Tethering
Now you know what could possibly happen. Also keep in mind that new ways to hack things are being developed every day, by the bad guys and the good guys.

Is it likely that you’re going to get hacked through tethering? There aren’t any statistics on that, but no one thinks they’ll get in a car accident either. The sad fact is that almost everyone gets in a car accident of some sort. If they’re lucky, it’s a paint chip. If they aren’t, it’s a life altering event. So, we all get insurance.
In the same mindset, be your own insurance against getting hacked through mobile hotspot tethering. Follow the advice above and keep an eye on your phone. Maybe you’ll be one of the lucky few that never has, or causes, an accident.
