Every piece of data that you fail to secure can be used against you
We use dozens of online services and applications every day to send and receive emails and text messages, make video calls, read news and watch videos online, and much more. And it’s extremely hard to keep track and secure the insane amount of data we produce and consume every day.
And in case you’re thinking, “I have nothing to hide,” you’re wrong. Every piece of data that you unleash in the web and fail to secure can be used against you. In the wrong hands, those data points can be gathered and correlated to create a digital profile, which can then be used to commit fraud, forgery and phishing attacks against you.
Your digital profile can also be used to invade your privacy in annoying and creepy ways such as showing you ads that are personalized based on your most intimate preferences and information.
However, it’s never too soon to start protecting your digital information from unwanted eyes. In this regard, your best friend is encryption, the science of scrambling data using mathematics. Encryption makes sure only intended people can read your data. Unauthorized parties who access your data will see nothing but a bunch of undecipherable bytes.
Here’s how you can encrypt all the data you store on your devices and in the cloud.
Encrypt Your On-Device Data
First, the easy part. You should start by encrypting the data you physically hold. This includes the content you store on your laptop, desktop PC, smartphone, tablet and removable drives. If you lose your devices, you risk placing sensitive information in the wrong hands.
The most secure way to encrypt your on-device data is full-disk encryption (FDE). FDE encrypts everything on a device and only makes the data available for use after the user provides a password or PIN code.
Most operating systems support FDE. In Windows, you can use BitLocker to turn on full-disk encryption on your PC. In macOS, the full-disk encryption is called FileVault. You can read our step-by-step guide on using BitLocker and FileVault.
Windows BitLocker also supports encrypting external drives such as memory cards and USB thumb drives. On macOS, you can use the Disk Utility to create an encrypted USB drive.
Alternatively, you can try hardware encrypted devices. Hardware encrypted drives require users to enter a PIN code on the device before plugging it to the computer. Encrypted drives are more expensive than their non-encrypted counterparts, but they are also more secure.
You should also encrypt your mobile devices. On-device encryption will make sure that an unauthorized person won’t be able to gain access to your phone’s data, even if they get physical access to it. Both iOS and Android support full-disk encryption. All Apple devices running iOS 8.0 and later are encrypted by default. We suggest you leave it that way.
The Android landscape is a bit fragmented since OS default settings and interfaces might differ based on manufacturer and OS version. Make sure to check yours is encrypted.
Encrypt Your Data in the Cloud
We rely on cloud storage services such as Google Drive, DropBox and Microsoft OneDrive to store our files and share them with friends and colleagues. But while those services do a good job to protect your data against unauthorized access, they still have access to the contents of the files you store in their cloud services. They also can’t protect you if your account gets hijacked.
If you don’t feel comfortable with Google or Microsoft having access to your sensitive files, you can use Boxcryptor. Boxcryptor integrates with most popular storage services and adds a layer of encryption to protect your files before uploading them to the cloud. This way, you can make sure that only you and the people you share your files with will be aware of their content.
Alternatively, you can use an end-to-end encrypted (E2EE) storage service such as Tresorit. Before storing your files in the cloud, E2EE storage services encrypt your files with keys that you exclusively hold, and not even the service that stores your files can access their content.
Encrypt Your Internet Traffic
Perhaps equally as important as encrypting your files is the encryption of your internet traffic. Your internet service provider (ISP)—or a malicious actor that might be lurking on the public Wi-Fi network you’re using—will be able to eavesdrop on the sites you browse to and the services and applications you use. They can use that information to sell it to advertisers or, in the case of hackers, use it against you.
To protect your internet traffic against nosy and malicious parties, you can sign up to a virtual private network (VPN). When you use a VPN, all your internet traffic is encrypted and channeled through a VPN server before reaching its destiny.
If a malicious actor (or your ISP) decides to monitor your traffic, all they’ll see is a stream of encrypted data exchanged between you and your VPN server. They won’t be able to figure out which websites and applications you’re using.
One thing to consider is that your VPN provider will still have full visibility on your internet traffic. If you want absolute privacy, you can use The Onion Router (Tor). Tor, which is both the name of a darknet network and a namesake browser, encrypts your internet traffic and bounces it through several independent computers running a specialized software.
None of the computers in the Tor network has full knowledge of the source and the destination of your internet traffic, which gives you full privacy. However, Tor comes with a considerable speed penalty, and many websites block traffic coming from the Tor network.
Encrypt Your Emails
I guess I don’t need to tell you the importance of protecting your emails. Just ask John Podesta, whose leaked emails might have cost his boss her chance at presidency. Encrypting your emails can protect your sensitive communications against people who gain unwanted access to them. This can be hackers who break into your account, or your email provider itself.
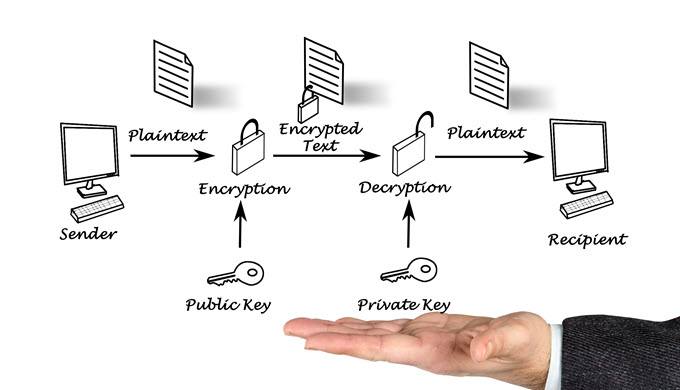
To encrypt your emails, you can use Pretty Good Privacy (PGP). PGP is an open protocol that uses public-private key encryption to enable users to exchange encrypted emails. With PGP, every user has a public, known to everyone, which enables other users to send them encrypted emails.
The private key, which is only known to the user and stored on the user’s device, can decrypt messages encrypted with the public key. If an unintended party intercepts a PGP-encrypted email, they won’t be able to read its contents. Even if they break into your email account by stealing your credentials, they won’t be able to read the contents of your encrypted emails.
One of the advantages of PGP is that it can be integrated into any email service. There plenty of plugins that add PGP support to email client applications such as Microsoft Outlook. If you’re using a web client like the Gmail or Yahoo websites, you can use Mailvelope, a browser extension that adds easy-to-use PGP support to most popular email services.
Alternatively, you can sign-up to an end-to-end encrypted email service such as ProtonMail. ProtonMail encrypts your emails without the need to take any additional steps. Unlike services such as Gmail and Outlook.com, ProtonMail won’t be able to read the content of your emails.
Encrypt Your Messages
Messaging apps have become an inseparable part of our lives. There are dozens of messaging services you can use to communicate with family, friends and colleagues. But they provide different levels of security.
Preferably, you should use a messaging service that is end-to-end encrypted. Nowadays, most popular messaging services provide end-to-end encryption. Some examples include WhatsApp, Signal, Telegram, Viber and Wickr.
However, those that enable E2EE by default are more secure. WhatsApp, Signal and Wickr enable end-to-end encryption by default.
Also, messaging services that are based on open-source protocols are more reliable because they can be peer-reviewed by independent industry experts. Signal Protocol, the E2EE technology that powers WhatsApp and Signal, is an open-source protocol that has been endorsed by many security experts.